
Mozilla released Firefox 87.0 this morning, the latest version of its open source web browser. Following on the heels of December's Firefox 85 and February's Firefox 86, the new version's most important features—Smart Block and improved referrer trimming—are privacy related.
Smart Block
Firefox has been blocking third-party tracking scripts by default for quite a while now. For the most part, this works pretty seamlessly—but in some cases, missing tracking scripts can interfere with a page's rendering, either delaying it (as seen in the animated image above, on the left) or permanently breaking it.
Smart Block takes an additional step to improve the rendering on pages that embed third-party trackers—instead of just pulling the script and leaving a "hole" where it used to be, Smart Block replaces it with what Mozilla describes as "stand-in" scripts. These stand-in scripts function just enough like the original trackers to restore the intended page-rendering sequence and results without actually leaking data to third parties.
Mozilla sources much of its data on what is—or is not—a "common tracking script" which needs a Smart Block stand-in from the Disconnect tracking protection list.
Improved referrer trimming
When you embed an image from some other website in your own website, information about your site's viewers leaks to the other website's operators. To illustrate this, let's imagine that the operators of greatsearch.tld, a fictitious search engine, include an image of a sheep from sheep-pictures.tld on every results page.
The HTML code for the embedded image is simple:
<img src=https://sheep-pictures.tld/sheep1.jpg>
When users of greatsearch.tld use that site, their browsers see that tag and automatically download https://sheep-pictures.tld/sheep1.jpg while rendering the page.

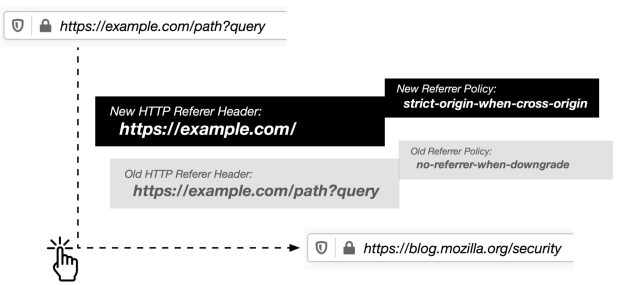
Traditionally, the entire URL of the referring page is included in that web request... which means information leakage to the operators of sheep-pictures.tld, who would see something like this in their logs:
240.163.255.110 - - [15/Mar/2021:10:28:57 -0400] "GET /sheep1.jpg
HTTP/1.1" 200 11676 "http://greatsearch.tld/res
ults?really-embarrassing-medical-condition"
Now that we understand the referrer field itself, it's pretty clear what "referrer trimming" means—and why Mozilla is getting more aggressive about it. If the user above were using Firefox 87 when making the same search, the operators of sheep-pictures.tld would instead see the following log entry:
240.163.255.110 - - [15/Mar/2021:10:28:57 -0400] "GET /sheep1.jpg
HTTP/1.1" 200 11676 "http://greatsearch.tld/"
Additional fixes and features
Firefox 87.0 also offers improvements in the Highlight All feature of Find in Page, full support for macOS' built-in screen reader VoiceOver, and several minor UI enhancements, security fixes, and general tweaks. For the full list, head on over to Mozilla's own Firefox 87.0 release notes.
reader comments
78