Researchers are warning of a critical remote code-execution (RCE) flaw in the Windows version of Cisco Jabber, the networking company’s video-conferencing and instant-messaging application. Attackers can exploit the flaw merely by sending targets specially crafted messages – no user interaction required.
The flaw (CVE-2020-3495) has a CVSS score of 9.9 out of 10, making it critical in severity, Cisco said in a Wednesday advisory. Researchers with Watchcom, who discovered the flaw, said that with remote workforces surging during the coronavirus pandemic, the implications of the vulnerability are especially serious.
“Given their newfound prevalence in organizations of all sizes, these applications are becoming an increasingly attractive target for attackers,” Watchcom researchers said in an analysis on Wednesday. “A lot of sensitive information is shared through video calls or instant messages, and the applications are used by the majority of employees, including those with privileged access to other IT systems.”
An attacker could exploit the flaw by sending specially crafted Extensible Messaging and Presence Protocol (XMPP) messages to vulnerable end-user systems running Cisco Jabber for Windows. XMPP is an XML-based protocol for instant messaging, based on an open standard, which is widely used in both open-source and proprietary software.
While attackers can be remote to launch such an attack, they may require access to the same XMPP domain or another method of access to be able to send messages to clients, according to researchers. However, for the most part, the attack is easy to carry out: No user interaction is required on the part of the targeted victim, and the vulnerability can be exploited even when Cisco Jabber is running in the background.
The issue stems from Cisco Jabber improperly validating message contents; the application does not properly sanitize incoming HTML messages. It instead passes the messages through a flawed cross-site scripting (XSS) filter. Researchers discovered that this filter could be bypassed using an attribute called “onanimationstart.” This attribute is used to specify a JavaScript function that will be called when an element’s CSS animation starts playing.
Using the attribute (along with a built-in animation assigned to it) researchers found it was possible to create malicious HTML tags that the filter did not catch, and were ultimately executed. As a final step, researchers created a malicious message using these HTML tags, that then intercepted an XMPP message sent by the application and modified it.
Attackers can do this manually on their own machine or it can be automated to create a worm that spreads automatically, said researchers.
Finally, “as a result of exploitation, an attacker could cause the application to run an arbitrary executable that already exists within the local file path of the application,” according to Cisco. “The executable would run on the end-user system with the privileges of the user who initiated the Cisco Jabber client application.”
Systems using Cisco Jabber in phone-only mode (without XMPP messaging services enabled) are not vulnerable to exploitation, Cisco’s advisory said. In addition, the vulnerability is not exploitable when Cisco Jabber is configured to use messaging services other than XMPP messaging.
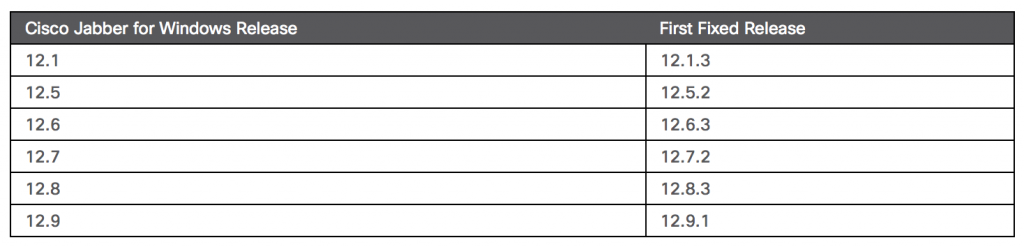
The vulnerabilities affect all currently supported versions of the Cisco Jabber client (12.1 – 12.9). Cisco has released updates for different releases of affected Cisco Jabber. See the fixes in the table below:
Researchers said that they found three other vulnerabilities in Cisco Jabber, including a protocol-handler-command infection (CVE-2020-3430), an information-disclosure flaw (CVE-2020-3498) and a Universal Naming Convention link-handling issue (CVE-2020-3537).
Cisco said it is not aware of any public announcements or malicious use of the flaw.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.