
Attackers using the Ragnar Locker ransomware have encrypted the systems of Portuguese multinational energy giant Energias de Portugal (EDP) and are now asking for a 1580 BTC ransom ($10.9M or €9.9M).
EDP Group is one of the largest European operators in the energy sector (gas and electricity) and the world's 4th largest producer of wind energy.
The company is present in 19 countries and on 4 continents, it has over 11.500 employees and delivers energy to more than 11 million customers.
Attackers threaten to leak 10 TB of stolen documents
During the attack, the Ragnar Locker ransomware operators claim to have stolen over 10 TB of sensitive company files and they are now threatening the company to leak all the stolen data unless the ransom is paid.
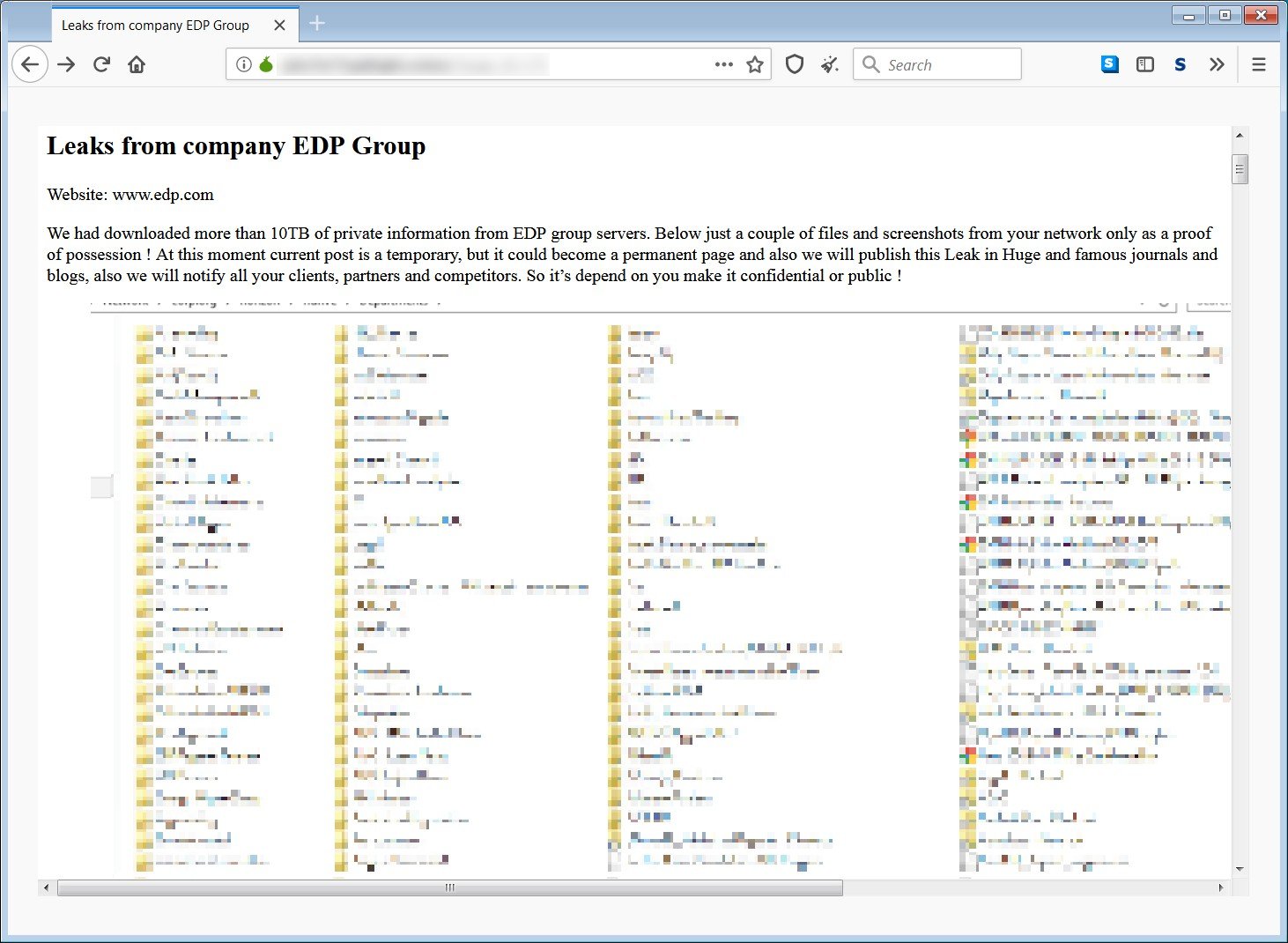
"We had downloaded more than 10TB of private information from EDP group servers," a new post on Ragnarok's leak site says.
"Below just a couple of files and screenshots from your network only as a proof of possession! At this moment current post is a temporary, but it could become a permanent page and also we will publish this Leak in Huge and famous journals and blogs, also we will notify all your clients, partners and competitors. So it’s depend on you make it confidential or public !"
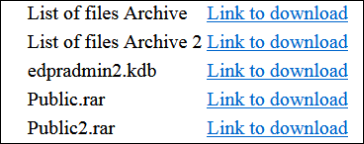
Among the already leaked files published as a sign of what's to come, the attackers included an edpradmin2.kdb file which is a KeePass password manager database.
When clicked on the leak site, the link leads to a database export including EDP employees' login names, passwords, accounts, URLs, and notes.
The Ragnar Locker ransomware sample used in this attack was found by MalwareHunterTeam and BleepingComputer was able to also find the ransom note and the Tor payment page where the attackers detail the decryption process and the ransom amount.
According to the ransom note dropped on the EDP encrypted systems, the attackers were able to steal confidential information on billing, contracts, transactions, clients, and partners.
"And be assure that if you wouldn't pay, all files and documents would be publicated for everyones view and also we would notify all your clients and partners about this leakage with direct links," the ransom note reads.
"So if you want to avoid such harm for your reputation, better pay the amount that we asking for."
.png)
EDP taunted in the live chat room
As also seen BleepingComputer, the Ragnar Locker operators taunted EDP in a live chat "client room" used by the attackers to communicate with their victims, asking them to "check the article about your company" on the data leak site and if the company is "ready to see your private information, at the breaking need, tech-blogs, and stockmarket sites."
They also added that the "timer is not waiting" and warned EDP not to attempt to decrypt their data using any other software besides the decryption tool provided by the Ragnar Locker operators as they risk damaging or losing it.
The attackers offered EDP a "special price" if they reach out within two days of their systems having been encrypted, however, they also warned that the company will have to wait for their turn as the ransomware's live chat is not online 24/7.
BleepingComputer has reached out to EDP for comment and additional details but had not heard back at the time of this publication. This article will be updated when a response is received.
Delivered via MSP enterprise support tools
Ragnar Locker ransomware was first spotted while being used as part of attacks against compromised networks towards the end of December 2019.
The Ragnar Locker operators target software regularly used by managed service providers to prevent their attack from being detected and blocked.
Kyle Hanslovan, the CEO of MSP security firm Huntress Labs, told BleepingComputer in February of his company seeing Ragnar Locker being deployed via the MSP software ConnectWise.
After reconnaissance and pre-deployment stages, the attackers drop a highly targeted ransomware executable that adds specific extension to encrypted files, features an embedded RSA-2048 key, and drops custom ransom notes.
The ransom notes include the victim's company name, a link to the Tor site, and the data leak site with the victim's published data.
BleepingComputer has previously seen multiple ransom notes for Ragnar Locker with ransoms ranging from $200,000 to roughly $600,000.
Update April 16, 09:21 EDT: An EDP spokesperson told BleepingComputer that the attack did not impact the company's power supply service and critical infrastructure.
EDP was the target of a computer attack on its corporate network this Monday, April 13th, which conditioned part of its services and operations. The power supply service and critical infrastructure, however, have never been compromised and we continue to ensure this operation as normal.
The situation is currently being assessed and we have teams dedicated to restoring the normal functioning of the systems as soon as possible, which is our priority.
EDP is working with the authorities, that were immediately notified of the attack to identify the origin and anatomy of the attack. At this moment, we have no knowledge of this alleged ransom demand - we have only seen this information disclosed in the media, which we cannot verify.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now